Telematics at KIT
Table of Contents
In this post I give a visual overview over the lecture “Telematik” at KIT and share my answers to the comprehension questions and the poll questions.
Topics of the lecture #
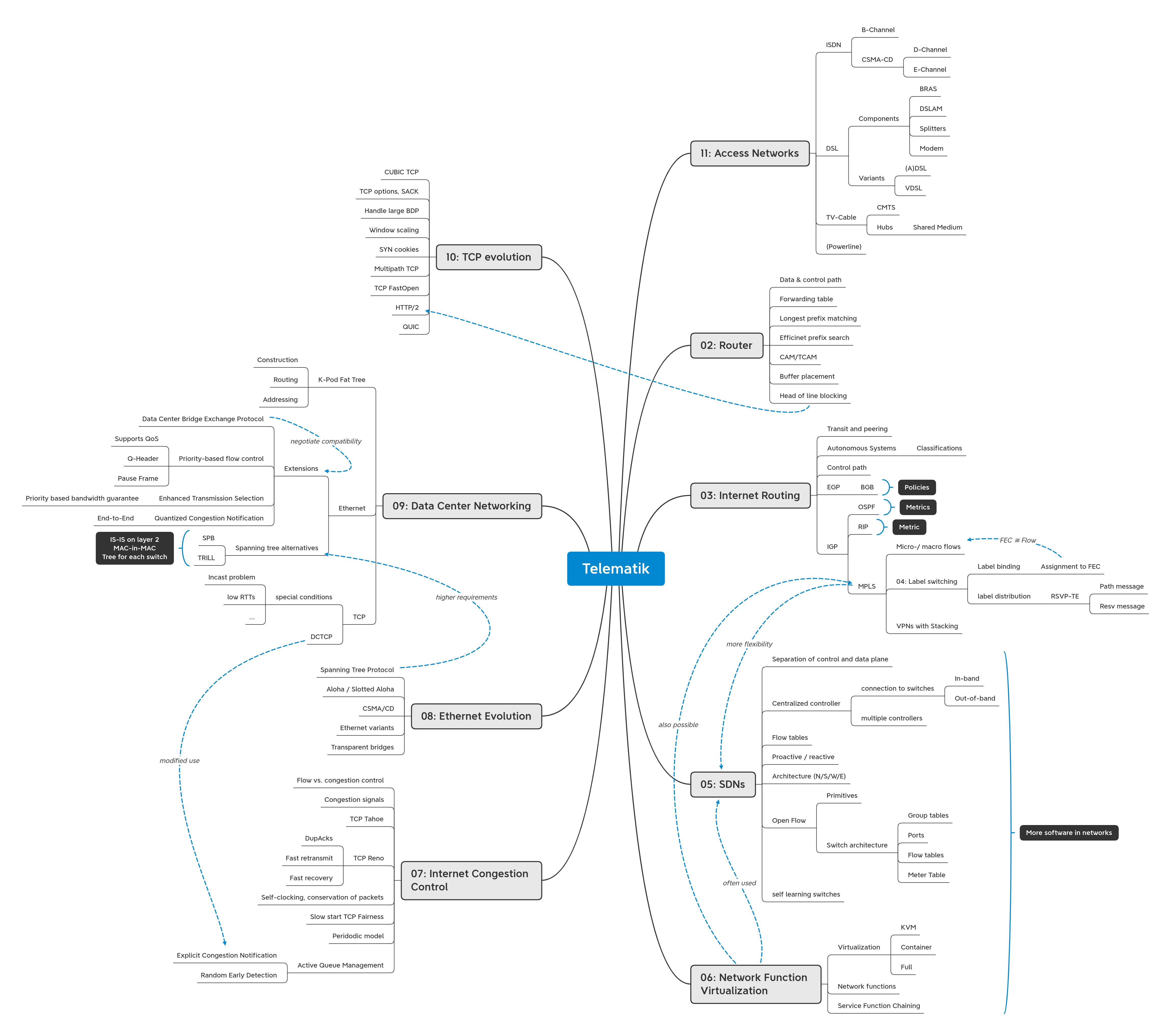
I use mindmaps like this to track learning process over all topics.
Comprehension questions #
You can compare your answers to mine, by expanding the toggles.
Disclaimer: I wrote most of this on a train ride with fogged glasses, so if you spot any mistakes or have anything to add, drop me a mail at wachter[punkt]blog[ätt]habmalnefrage[punkt]de
Chapter 02 - Router
-
What are important responsibilities of the network layer?
Global structured addressing of end system, routing, fragmentation of data (at least for packet oriented communication)
-
Which basic operations are usually performed by an IP router in order to forward a packet to its destination?
Verify checksum and header length, decrement time to live, lookup output port in the forwarding table and send out datagrams and with recalculated checksum. Possibly fragmentation has to happen. With IP options weird things can happen, but those are not in wide use today.
-
Why are high link-speeds such a big problem for modern forwarding hardware?
The goal is to perform forwarding at line speed, even for small packages, like acks. Therefore, the lookup in the forwarding table must happen fast, also for blocking situations and peak load there must be large and fast buffers.
-
How does longest prefix matching work in general?
Select the most specific entry. That is the entry with the longest prefix of a concrete address i.e. the one with the least don't care digits.
-
What are efficient (software) data structures for handling longest prefix matching and how do they work?
- A simple array is not the most efficient data structure for big tables, but easy to implement on small embedded systems and therefore has it's raison d'etre.
- Binary tries are
sorted binary search trees with some nodes being valid prefixes. The last node that is the longest
prefix. There are
several variations.
- Path compression: Speed and memory improvements for sparse trees
- Multibit trie: Compare more than one bit at a time (typically 4, not binary anymore)
- Hash tables have fast lookup speed, but are not designed for longest prefix matching.
-
In what way can hash tables support a trie-based address lookup?
Hash tables can store lookups results and therefore act as a cache.
-
What is a TCAM?
TCAM stands for ternary content addressable memory. Given a value, a TCAM can determine the rows that a prefix of the given value is stored in. If sorted by longest prefix, TCAMs can be used for longest prefix matching.
-
What are the main benefits and problems of the TCAM technology?
- Benefit: lookups in one clock cycle
-
Problems
- High energy consumption
- High cost
- Strict ordering makes updates hard and therefore TCAMs don't scale
-
Where can buffer elements be placed inside a switch? What are the associated benefits and drawbacks?
- Input
buffer
- Benefit: Easy to implement
- Drawback: Head of line blocking
- Output
buffer
- Benefits: No head of line blocking, theoretically 100% throughput
- Drawback: High hardware requirements for switch fabric and buffer memory
- Distributed
buffers
- Benefit: No head of line blocking, optimal throughput in practice
- Drawback: Higher memory requirement
- Central
buffer
- Benefit: Low memory requirement
- Drawback: Central buffer must be fast memory
- Input
buffer
Chapter 03 - Internet Routing
-
What is the difference between control path and data path?
- Control path: distribute routing information and other information about the network
- Data path: forward data from higher layers, usually wrapped in IP datagrams
-
What information is stored in the routing table, what in the forwarding table? Compare routing policy and routing metric. What are the similarities, what are the differences?
- Routing table: subnet, IP address of next hop to this subnet
- Forwarding table: prefix, output port
-
Compare routing policy and routing metric. What are the similarities, what are the differences?
The both are the basis for the routing decision. Routing metrics are measurable, while routing policies are high level decisions by the network operator.
-
Which problems can occur if the routing is (solely) based on the current delay metric? How can these problems be solved?
Problem: jitter. Solution: moving average
-
Why does the Internet need autonomous systems?
Autonomous systems allow for an abstract view of the network which improves scalability. Also, with autonomous systems every operator has the freedom internally use their own protocols.
-
Can you get an AS number for your home network?
Using
traceroute -Ayou can the AS numbers of the hops to a destination. AS numbers are assigned by the ripe in Europe only to multi-homed ASes.
-
In which way can an autonomous system be classified (there might be several categories!) ?
- By connections to other autonomous
systems.
- StubAS
- Multi-home AS
- Transit AS
Or by peering policy, or by economic position: tier 1, tier 2, tier 3
- By connections to other autonomous
systems.
-
Is private peering free of charge? What about public peering?
For private peering the autonomous systems don't pay for direct traffic, but still for transit traffic. Also, there has to be a link between autonomous systems.
-
What are the main benefits of public peering compared to transit?
- Public peering is less expensive, as there are only operation cost for the IXP.
- Only few central knots (IXPs) needed instead of a tight mesh.
- Small autonomous systems, do not need individual private peering contracts with big ISPs.
-
What is an IXP?
IXP stands for internet exchange point. IXPs allow public peering between autonomous systems at a central point.
-
Where does an ISP use interior gateway protocols? Where exterior gateway protocols?
Interior gateway protocol is used within the AS. Exterior gateway protocol ist used for communications with other autonomous systems.
-
What transport protocol does RIP use? What about OSPF?
RIP: UDP, OSPF: no transport protocol, direct use of IP
-
Would it be possible to use RIP as the only routing protocol for the whole Internet? What about OSPF?
Both no. RIP is limited to 15 hops. For OSPF every router needs to know the whole network topology.
-
What is stored in the link state database?
The newest Link State Advertisements for all routers in the network.
-
Which information is gathered by the hello protocol?
The liveliness of the adjacent routers. Requires a bi-directional direct connection.
-
What will happen if all control plane messages in an OSPF network start being dropped after the network was operational for some time? When will the network stop forwarding packets? When will the link-state databases be emptied?
LSAs have a time to live of 30 minutes
-
Why does a new OSPF router synchronize its database before participating in OSPF LSA exchange? What would it have to do if the mechanism was not available?
So that they do not send old false information to other OSPF routers.
-
How can BGP save routing messages via aggregation?
Routes are grouped together in a single prefix, if they are similar and reach the same destination. Now not every route has to be announced.
-
For what purpose do we need IBGP?
To automatically build transit routes through an AS.
-
Do the SYN and SYN-ACK packets of a TCP handshake with a public server on the Internet visit (always) the same routers?
No, the route may change in the meantime. E.g. because of load balancing
-
Why does the BGP routing process requires multiple (logical) tables such as Adj-RIB-In and Adj-RIB-out?
Routing decisions are made by the policy engines (not metric based). For them to have all available information for every peer there exists separate tables.
-
Is it possible to intercept all traffic towards and from an ISP without alerting the operators working at the ISP?
This very much depends on the capabilities of the attacker. An attacker that controls all the physical cables can easily do this. Another AS may announce longer prefixes and thereby intercept all traffic, but the ISP will notice that by checking the announcements for it's own prefixes.
-
Why is the routing table of a BGP router in the default free zone so big?
The internet get bigger there are more muli-homed/transit ASes. Also, because of IPv4 address scarcity there exist many small prefixes that must be propagated.
Chapter 04 - Label Switching
-
Explain the basic concepts of label switching.
Do not route based on IP address only. Instead, establish flows and label each packet with a locally unique ID. Every router in the local network acts as a virtual circuit and makes routing decision only based on the label. This combines the ideas of packet switching and circuit switching.
-
Which goals are pursued by label switching?
More flexible, faster lookups, because are chosen locally and therefore can be short.
-
How can data streams be aggregated by MPLS?
Data streams that should be treated equally are aggregated into forwarding equivalence classes (≅ flows) equivalence classes are encoded in the assigned labels
-
How can the IP data stream be mapped to different MPLS tunnels within the label edge router?
They are put in different forwarding equivalence classes.
-
Which operations can be performed on labels?
Label binding and label distribution
-
Explain the label operations that happen when a packet travels through an MPLS domain.
Label enters at edge router. Then label binding happens, meaning a label is assigned to a forwarding equivalence class. This label must be distributed in the network this can either be done by unsolicited downstream or by downstream on demand. The dominating protocol used here is RSVP-TE. Then the packet can be sent through the network. Routing decision are based on the forwarding equivalence class of a label.
Chapter 05 - Software-defined Networks
-
What are the basic principles behind SDN? Explain each of them shortly!
Separation of data plane realized by the controller and control plane realized on the switch. The SDN controller makes all routing decisions by installing rules in the flow tables of the connected SDN switches or even deciding for some individual packets. This can happen either reactive or proactive flow programming. `
-
What is the „flowspace“ and how does it relate to SDN?
Not sure but I guess a flowspace is the possibly overlapping area of responsibility of one controller.
-
Would you consider using microflows or macroflows, if the available flow table space of the switches in your network is heavily limited? What trade-off do you have to keep in mind?
Microflows are very fine-grained therefore much more rules in the flow table are needed. So if memory is an issue macroflows are preferred at the cost of fine granularity.
-
Is it possible to combine the use of macroflows and the reactive mode of operation?
Yes, it is. The rules can be installed at any time.
-
List and explain the elements of a rule and a flow table entry.
Match - On what packets should the rule be applied? Table - In what flow table at the switch should the rule be put? Action - What should happen with the packet e.g. send to controller, forward at specific interface, drop, check another flow table. Priority - If there are overlapping rules (multiple matches for a packet) the one with the highest priority is used. Counters - Increments if the rule was applied. Timeout - Lifetime of a rule. Cookie - Identifier of a rule for the controller. Flags - Flow management information
-
Give an example for an SDN app that uses proactive flow programming. Use the SDN pseudo programming language!
onConnect(S _switch) { r = Rule(); r.MATCH('*'); r.PRIORITY(0); r.ACTION('CONTROLLER'); send_rule(r, _switch); r1 = Rule(); r1.MATCH('IP_DST', '42.23.7.0/8'); r1.PRIORITY(1); r1.ACTION('OUTPUT', 1); send_rule(r1, _switch); }
-
Give an example for an SDN app that uses reactive flow programming. Use the SDN pseudo programming language!
onConnect(S _switch) { r = Rule(); r.MATCH('*'); r.PRIORITY(0); r.ACTION('CONTROLLER'); send_rule(r, _switch); r1 = Rule(); r1.MATCH('IP_DST', '42.23.7.0/8'); r1.PRIORITY(1); r1.ACTION('OUTPUT', 1); send_rule(r1, _switch); }
-
Briefly sketch the layered SDN architecture and explain the function of the different interfaces (southbound, northbound, ...)
For a sketch see the slides. Northbound - communication with the apps. Southbound - Communication with the SDN switches. Eastbound - Communication with legacy hardware. Westbound - communication with other SDN controllers.
-
What is OpenFlow? Is there an OpenFlow counterpart in the „non-SDN“ world? For what purpose does OpenFlow need reserved ports?
A specific protocol and standard for SDN programming. In non-SDN world there are also protocols for central switch configuration. Most prominent these days: SolarWinds NCM.
-
Give two example for controller-to-switch messages
send_rule,send_packet
-
What were the main problems with the different learning switch examples? What were the solutions?
See slides p.77 ff.
-
Is it possible in the SDN pseudo programming language to extract (only) the 10th packet of every TCP flow?
Yes, send every TCP packet to the controller and keep a data structure there. Doing this with less communication overhead may be done using the counter field in the flow table.
-
Can you think of two (conceptually different) use cases where the group table functionality is required?
Fast failover (FAST-FAILOVER Group), Load balancing (SELECT Group)
-
Consider a simple flow between H1 and H2 (identified by IP source and IP destination) that passes five SDN switches. How can this be programmed with the SDN pseudo programming language from the lecture, if a reactive approach should be used and a static getOutputPort(switch, IP) function is available? (MAC address resolution can be ignored)
onConnect(S _switch) { r = Rule(); r.MATCH('*'); r.PRIORITY(0); r.ACTION('CONTROLLER'); send_rule(r, _switch); } onPacketIn(P packet, S _switch, I inport) { r = Rule(); int port = getOutputPort(_switch, packet.IP_DST); r.MATCH('IP_DST', packet.IP_DST); r.PRIORITY(1); r.ACTION('OUTPUT, port); r.send_rule(r, _switch); r.send_packet(packet, _switch); }
-
What are the two different modes to exchange control messages between an SDN switch and an SDN controller?
Out-of-band, In-band
-
Why do we need distributed controllers?
To avoid a single controller being the bottleneck of the network (both in terms of scalability and reliability) and separation of concerns for different parts of the network.
-
Give an example how the controller can support separation of concerns by using an abstract view
The controller can provide different details about the network to different apps. So the individual apps only get the information that they need to get.
-
Give a brief sketch of the reactive and proactive load balancing approaches presented in the lecture
Unsure.
-
Name and explain at least two challenges of SDN with respect to the data plane, the control plane and the applications
Control to data plane: Controller — switch connectivity, control plane: controller is a bottleneck (single point of failure), control plane: special switches required, data plane & apps: consistency and communication in case of multiple controllers ( CAP-theorem)
Chapter 07 - Internet Congestion Control
-
Why are buffers needed in routers and switches?
To account for burst in network traffic that can not be processed / relayed on a slow link fast enough
-
Do large buffers have any disadvantages?
In case of a major congestion packets don't get dropped, but arrive late. At this time there might already have been a retransmission which leads to duplicate packets and out of order packets.
-
What is the difference between “goodput” and “throughput”?
Toughput: the total amount of data sent. Goodput: Application layer data sent (without headers and packets only used on lower layers.
-
Can it happen that throughput is high but goodput is low? Explanation!
Yes, there are multiple scenarios possible where this could be the case. The simplest example is bad protocol design: large headers, a lot of housekeeping messages, etc. But also in regular TCP-IP connection this can happen if multiple packets get lost, there are a lot of retransmissions, as TCP Reno only supports fast retransmit for one lost packet. In this case delivered packets are dropped at the receiver and do not reach the application layer.
-
Explain the tasks of flow control and congestion control.
Flow control manages to load of the receiver: Do not send more data than the receiver can process. Congestion control manages the load of the network in between sender and receiver: Send data just below the limit of the networks' capacity.
-
What does conservation of packets mean?
Always have a full window of (unacknowledged) data in transmit.
-
What is the difference between “congestion control” and “congestion avoidance”?
Congestion avoidance is a phase in congestion control where there is a linear increase in send data.
-
How can unfairness be quantified? Why is this important?
Jane's fairness index. Full efficiency on a link is not the only goal. Also make sure that every connection is able to transmit data.
-
Which kind of congestion control is used in the Internet?
CUBIC TCP, BBR is supported since Linux 4.9.
-
Which problems did TCP Tahoe solve?
TCP Tahoe was the first congestion control algorithm and is able to detect congestions without classifying them.
-
Which problems did TCP Reno solve?
TCP Reno classifies congestions in major congestions (timeouts) and minor congestions (duplicate acks). Minor congestions do not lead to going back to slow start.
-
Explain the periodic model? What are the basic assumptions that are applied?
The periodic models approximately describes long-lived TCP connections that are in steady state. A constant loss probability p is assumed. The network drops every ( 1-1/p)th segment.
-
In ECN, what is the difference between “CE” and “ECE”?
"CE" stands for "congestion experienced". IP datagrams are marked as CE by a router that experiences a congestion. The receiver then sets the ECE flag in the TCP header of the ack that is sent back.
-
Describe a scenario that leads to duplicate acknowledgements.
If an ack takes loo long to deliver. The sender resends the packet that was already acked. Now to first ack arrives and the ack for the resent packet follows.
-
Explain, how AIMD converges.
AIMD as used by TCP Tahoe leads to a (kind of) saw tooth curve where there is an exponential and a linear part of every rising flank. In the linear part starts at SSThresh wich is FlightSize/2 of the last congestion.
-
True or false? After a timeout of the retransmission timer, the SSThresh value is always smaller as its previous value?
False, the network capacity might have increased during the current rising flank, so more packets were in flight than previously.
Poll Questions #
Live Session 1 #
Routing is task of. #
Layer 3, not Layers 4,2,1
The information in the forwarding table is „produced“ by #
Self-learning of addresses during packet transmission
System administrator ✔️ in some cases manually configures the routing table, which is the basis for the forwarding table
Routing protocol ✔️
IP protocol
DHCP protocol
Which of the following characteristics are important with respect to packet forwarding performance #
Number of entries ✔️
Time to search for an entry ✔️
Time to delete an entry
Time to include an entry
Prefix length ✔️
Amount of memory required ✔️
Live Session 2 #
The T in TCAM stands for #
Temporary ✔️
Telecom
Tenacious
Ternary
Timed
Taxonomic
Tentative
Why do network operators use TCAM? #
Cheaper than DRAM/SRAM
Faster lookups ✔️
Can store more prefixes
Support for encryption
Mandatory because of longest prefix matching (mandatory compared to CAM, but there are other techniques such as tries)
Low energy footprint
Blocking in this context refers to #
In this session IP datagrams in routers are discussed but there is also head of line blocking in TCP e.g. when HTTP/2 traffic is transmitted
Packets of layer 4
Packets of layer 3 ✔️
Packets of layer 2
At layer 4, packet loss due to blocking leads to #
Retransmissions ✔️
No Retransmissions
Live Session 3 #
An OSPF router sends its link state information to its neighboring nodes. #
Yes
No ✔️ bit of an unclear question: initially the router sends the LSA to its neighbor, but those then forward it to the other routers.
An OSPF router has a global view on the network topology. #
Yes ✔️ in its OSPF domain with a short delay
No
OSPF floods hello messages in the network #
Yes
No ✔️ hello is used to establish a bidirectional connection between two adjacent routers. (LSAs are flooded)
OSPF area 1 is directly connected to OSPF area 2 #
Yes
No ✔️ area 0 is in between
Live Session 4 #
What can an AS do if it has detected that some of its own prefixes are “stolen” by another AS? #
Try to contact the malicious AS and ask to fix the error ✔️ if the AS has done this by accident
Contact ICANN and have the error corrected
Call the Internet police and report the theft
Try to “retrieve” the prefixes with Longest Prefix Matching? ✔️
Use other prefixes
Report the abuse to the upstream ASs and claim that there is an error ✔️
Transit (paid connectivity between two ASes) often uses a volume based billing scheme. But who has to pay? #
Depends on the point of view.
The upstream AS ️
The downstream AS ✔
Both
The following holds for BGP sessions #
Exist between BGP routers of neighboring ASes ✔️ usually, but needs to be esablished first with an open message and can be cut at any time with a notification message
Exist between BGP routers within an AS
Located on top of IP ✔️ TCP is on top of IP
Located on top of UDP
Located on top of TCP ✔️
How can a data stream on the Internet be uniquely identified? #
2 tuple
4 tuple
5 tuple ✔️ (Src_IP, Des_IP, Src_Port, Des_Port, protocol)
7 tuple
Which of the statements is correct? MPLS is #
Connectionless
Connection oriented ✔️
Capable of supporting traffic engineering ✔️
Circuit switched
Packet switched ✔️
Reliable
Based on longest-prefix matching
Which of the following match items may be used for classification purposes in MPLS? #
Information must be in headers
Port 80 ✔️
127.13.9.17/27 ✔️
Costs: xyz € per second
HTTPS ✔️
Green traffic only
This customer only after 6pm
Ethernet broadcast ✔️
The following MPLS label switching domain is given. The label switching path A1 – G2 – H3 – J4 is already established. Which of the following new label switching paths can be established? #
A1 – G1 – H1 – J1
A2 – G2 – H2 – J2
A3 – G1 – H1 – J1 ✔️
Session 5 #
What is the problem with the code below? #
The code will not work
The match part of the rule is missing
The rule should use “inport” instead of “outport”
The approach is inefficient ✔️
import getOutputPort
onPacketIn(packet, switch, inport) {
outport = getOutputPort(packet)
r = Rule()
r.ACTION('OUTPUT'‚ outport)
send_packet (packet, switch, r)
}
Something is wrong with this OpenFlow architecture figure. What is it? #
There is something wrong with …
the control channel ✔️ there should be a controller at the other end
the flow table pipeline ✔️
the ports
the routing table ✔️ should be meter table
the group table
Multiple distributed controllers can help with: #
Scalability ✔️
Resilience ✔️
Controller connectivity ✔️
Controller synchronization
Consistency
Flow table capacity
Flow setup latency
What is a „Network Slice“ #
Virtual network that is used by customers
Special „virtual application“ layer in the OSI model
Distinct section of a large physical network ✔️
Mapping between virtual switches / infrastructure and their physical counterpart
Session 7 #
Server S sends data to client C: Segment with sequence number seq is sent. Does the next segment that is sent by S always have the sequence number seq+1? #
Yes
No ✔️
Server S sends data to client C :Segment with sequence number seq=127 and 10 bytes of payload is sent. Does this segment has to include the acknowledgement number ack=137? #
Yes
No ✔️
Server S sends data to client C in the following sequence #
- Segment with sequence number seq=130 … is received
- Segment with sequence number seq=185 … is lost
- Segment with sequence number seq=253 … is received
Which acknowledgement number is included in the next segment sent from C to S?
130
131
185 ✔️
36
186
253
254
In self clocking segments are sent … #
always as soon as new data is available
at fixed time intervals
when receiving an acknowledgement ✔️
when the receive window is empty
Congestion Control is not needed #
in very fast networks
in very slow networks
if flow control windows (in total) are smaller than the bandwidth-delay-product
for small DNS queries ✔️
Congestion Avoidance #
finds the optimal operating point for a TCP connection will always go beyond at some point
keeps a TCP connection in a reasonable operation range ✔️
quickly brings a TCP connection in a reasonable operation range this is what slowstart is for
avoids packet loss will happen at some point
Session 8 #
In order to increase its bandwidth share, an unfair sender #
can open multiple TCP connections to the same destinations ✔️
can increase CWnd, even if it contradicts TCP standard ✔️
can send data without congestion control ✔️
will be detected quickly, by security/monitoring in routers not all of it can be quickly detected
Two TCP connections are considered fair to each other, if #
They achieve roughly the same data rate (on average) ✔️
They achieve roughly the same CWnd size (on average)
Each connection gets as much data rate as it needs
Each connection gets the same packet loss rate
Two competing TCP Reno connections usually achieve/get #
Roughly the same data rate (on average) only for same RTT and same MSS
Roughly the same CWnd size (on average) ✔️ measured in MSS
Exactly the data rates they need
The same packet loss rate
Two TCP senders (A and B) share a bottleneck. Sender A uses TCP Reno. RTT(A) = 2*RTT(B). How can sender A achieve (roughly) the same data rate? #
Use one TCP Reno connection
Use one TCP Tahoe connection
Use two TCP Reno connections ✔️
Halve its MSS
Jain’s fairness index #
Allows for weighted allocations among connections
Interprets fairness as achieving equal data rates for all connections sharing a bottleneck ✔️
Is only applicable in case of same RTT for all connections
Considers application limited connections
Session 9 #
How can a collision occur within a CSMA-based protocol? #
Two systems start sending at exactly the same time ✔️
One system starts sending while the complete medium is in use by another system
One system starts sending before the signal of another system reaches it ✔️
Which of the following mechanisms belongs to flow control? #
Stop-and-Wait ✔️
Slow Start
Sliding Window ✔️
RED
Pause function ✔️
The tasks of the Spanning Tree Protocol comprise … #
Configuration of a tree topology ✔️
Increasing the span of a LAN ✔️ is the result of it
Creating entries for the forwarding table
Selecting a root bridge ✔️
Which is the same for all Ethernet standards discussed in the lecture? #
Maximum achievable data rate
Encoding on layer 1
Frame format ✔️
Size of padding field ✔️
Session 10 #
The Incast communication pattern #
“request” direction is critical regarding congestion control
“response” direction is critical regarding congestion control ✔️
typically observed in case of back-up traffic
typically observed in applications making use of MapReduce ✔️
Why do we need to make changes to traditional TCP congestion control for data center environments? #
high number of concurrent TCP streams
low RTTs ✔️
high data rates
switches with large buffers
What applies to DCTCP? #
DCTCP estimates the congested fraction of the traffic ✔️
DCTCP modifies ECN ✔️
DCTCP requires changes to switches ✔️ but RED implementations be used as a basis
DCTCP requires changes to end systems ✔️
How many links do we need for a K-pod fat tree topology (excluding links to servers)? #
2 * k^3
1⁄2 * k^3 ✔️
k/2 + k^3
5/4 * k^2
Session 11 #
Selective acknowledgements (SACK) #
Replace standard TCP acknowledgements
Acknowledge out-of-order data ✔️
Acknowledge each TCP segment individually
Must be negotiated during connection establishment ✔️
What is required for TCP SYN cookies? #
Additional memory
Cryptographic hash functions ✔️
Explicit client-side support
Additional TCP options
With Multipath TCP #
Different physical paths can be used for a TCP connection ✔️
Different interfaces can be used for a TCP connection ✔️
TCP Reno is used as congestion control coupled congestion control, which behaves like Reno over all
CUBIC TCP is used as congestion control
A TCP connection has been established between end systems A and B. Which components directly limit the achievable data rate from A to B? #
Congestion window of A ✔️
Receive window of A
Congestion window of B
Receive window of B ✔️
Buffer of routers in between indirect limitation
Session 12 #
Why does ISDN requires an Echo channel, but Ethernet does not? #
ISDN uses bus topology ✔️
ISDN uses space division multiplex ✔️
ISDN uses twisted pair cable
ISDN uses AMI code ✔️ IAMI
Which multiplexing is used by ISDN? #
Frequency division multiplexing
Space division multiplexing ✔️
Time division multiplexing ✔️
Code division multiplexing
Wave length division multiplexing
What is NOT a component in a DSL installation #
Splitter
Copper twin conductor
DSLAM
Network termination ✔️
DSL modem
Adaptor ✔️
S0-Bus ✔️
Digital telephone switch
The BRAS is responsible for #
Routing traffic to/from broadband access devices ✔️
Support of quality-of-service ✔️
IP address assignment for clients ✔️
Power supply for subscriber installation